SSO using OIDC
Email contact@wandb.com to configure an Auth0 tenant for you with identity providers supported by W&B (such as SAML, Ping Federate, Active Directory, and more).
If you already use Auth0 or have an Open ID Connect compatible server, follow the instructions below to set up authorization with Open ID.
W&B Server operates with manual user management by default. Licensed versions of wandb/local also unlock SSO.
Open ID Connect
wandb/local uses Open ID Connect (OIDC) for authentication. Based on your use case, select one of the tabs to learn how to set up AWS Cognito or Okta authenticate W&B Server with Open ID Connect.
Select either a Single Page or Public Client application in your identity provider (IdP).
- AWS
- Okta
Follow the procedure below to set up AWS Cognito for authorization:
- First, sign in to your AWS account and navigate to the AWS Cognito App.
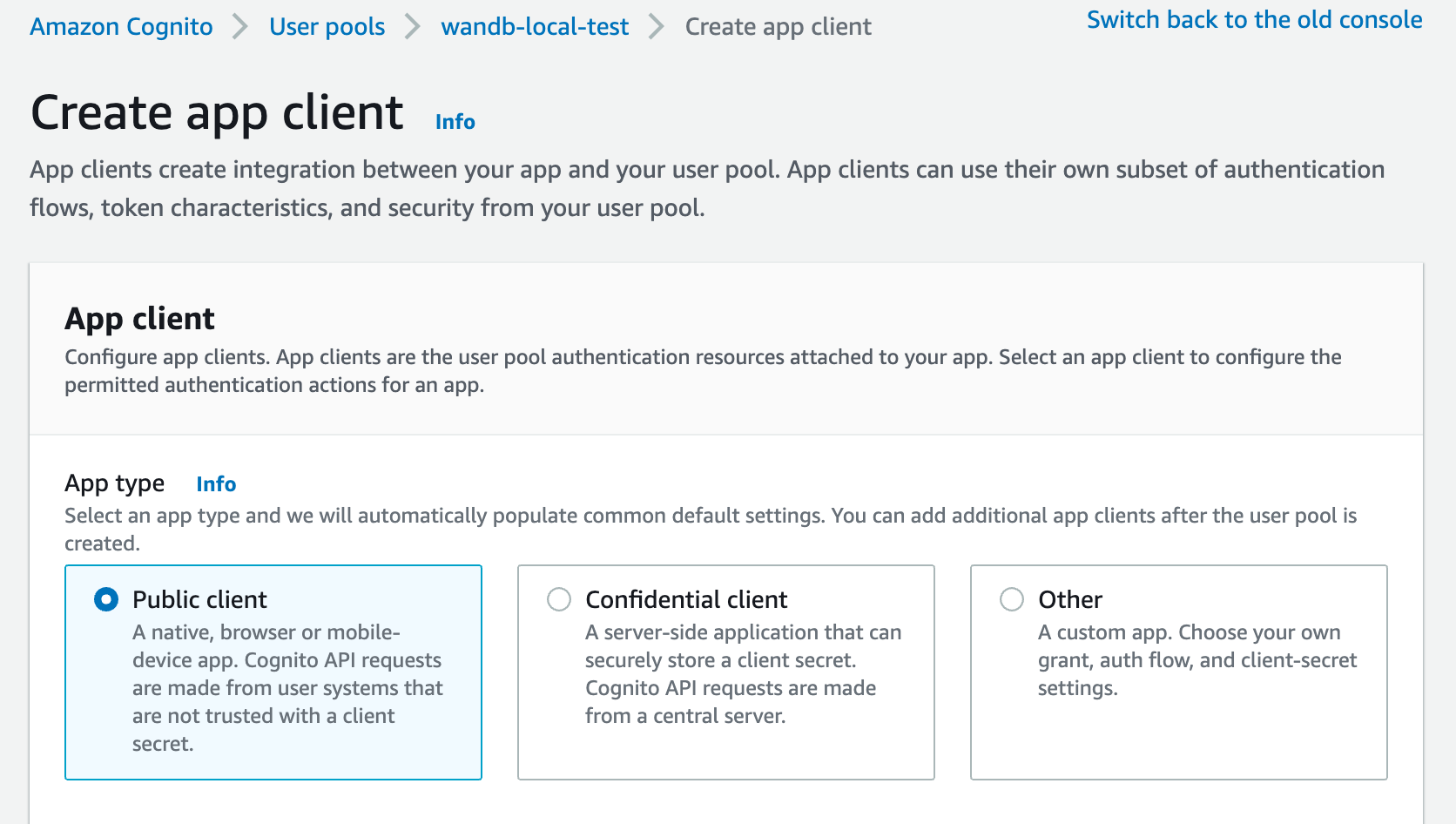
Provide an allowed callback URL to configure the application in your IdP:
- Add
http(s)://YOUR-W&B-HOST/oidc/callbackas the callback URL. ReplaceYOUR-W&B-HOSTwith your W&B host path.
- Add
If your IdP supports universal logout, set the Logout URL to
http(s)://YOUR-W&B-HOST. ReplaceYOUR-W&B-HOSTwith your W&B host path.
For example, if your application was running at https://wandb.mycompany.com, you would replace YOUR-W&B-HOST with wandb.mycompany.com.
The image below demonstrates how to provide allowed callback and sign-out URLs in AWS Cognito.
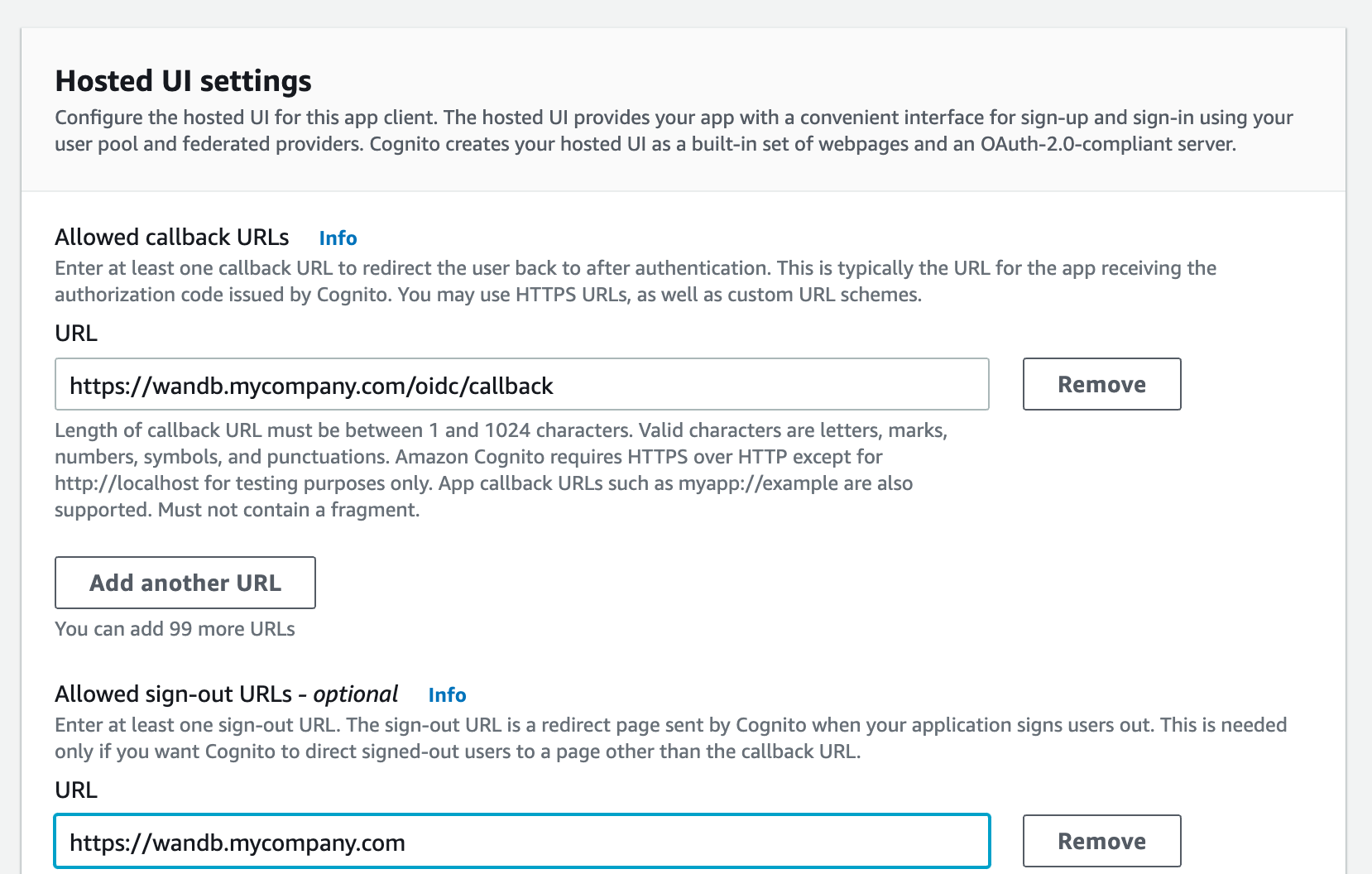
wandb/local uses the "implicit" grant with the "form_post" response type by default.
You can also configure wandb/local to perform an "authorization_code" grant that uses the PKCE Code Exchange flow.
- Select one or more OAuth grant types to configure how AWS Cognito will deliver tokens to your app.
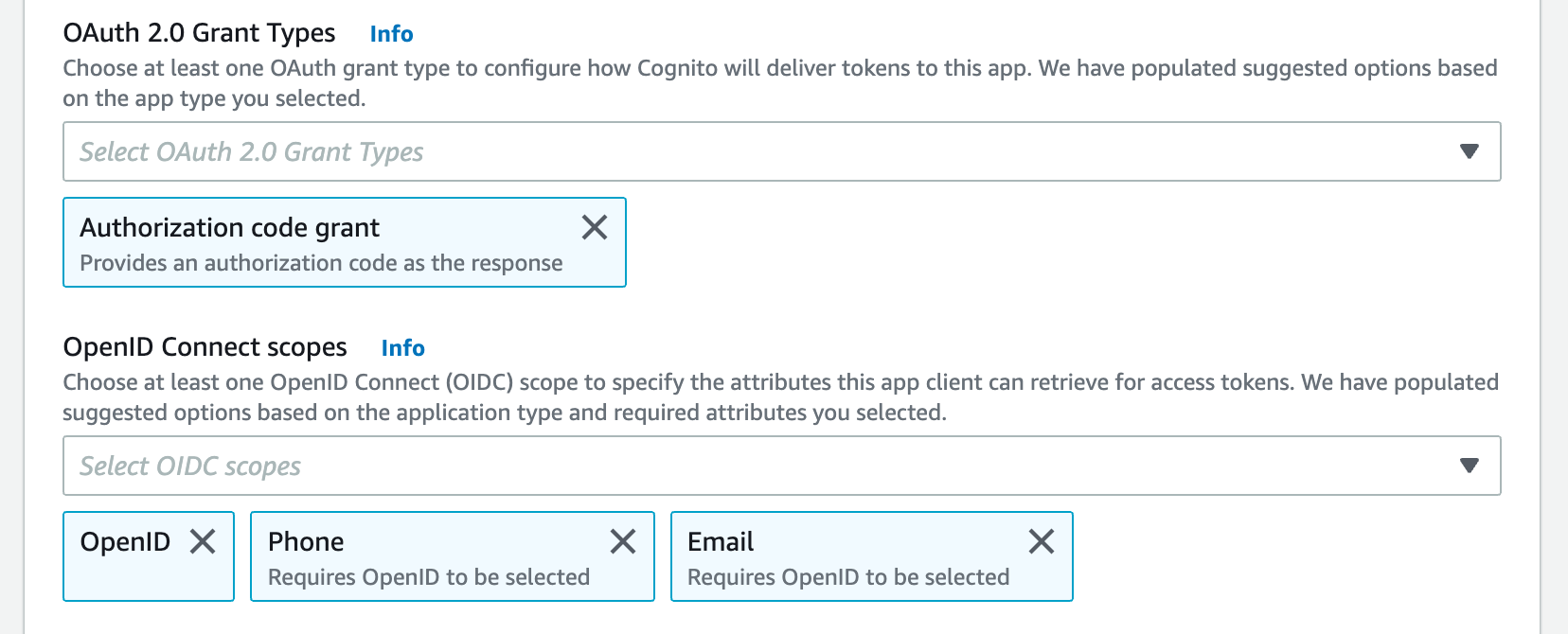
- W&B requires specific OpenID Connect (OIDC) scopes. Select the following from AWS Cognito App:
- "openid"
- "profile"
- "email"
For example, your AWS Cognito App UI should look similar to the following image:
Select the Auth Method in the settings page or set the OIDC_AUTH_METHOD environment variable to tell wandb/local which grant to.
For AWS Cognito providers you must set the Auth Method to "pkce"
- You need a Client ID and the URL of your OIDC issuer. The OpenID discovery document must be available at
$OIDC_ISSUER/.well-known/openid-configuration
For example, with AWS Cognito, you can generate your issuer URL by appending your User Pool ID to the Cognito IdP URL from the App Integration tab within the User Pools section:
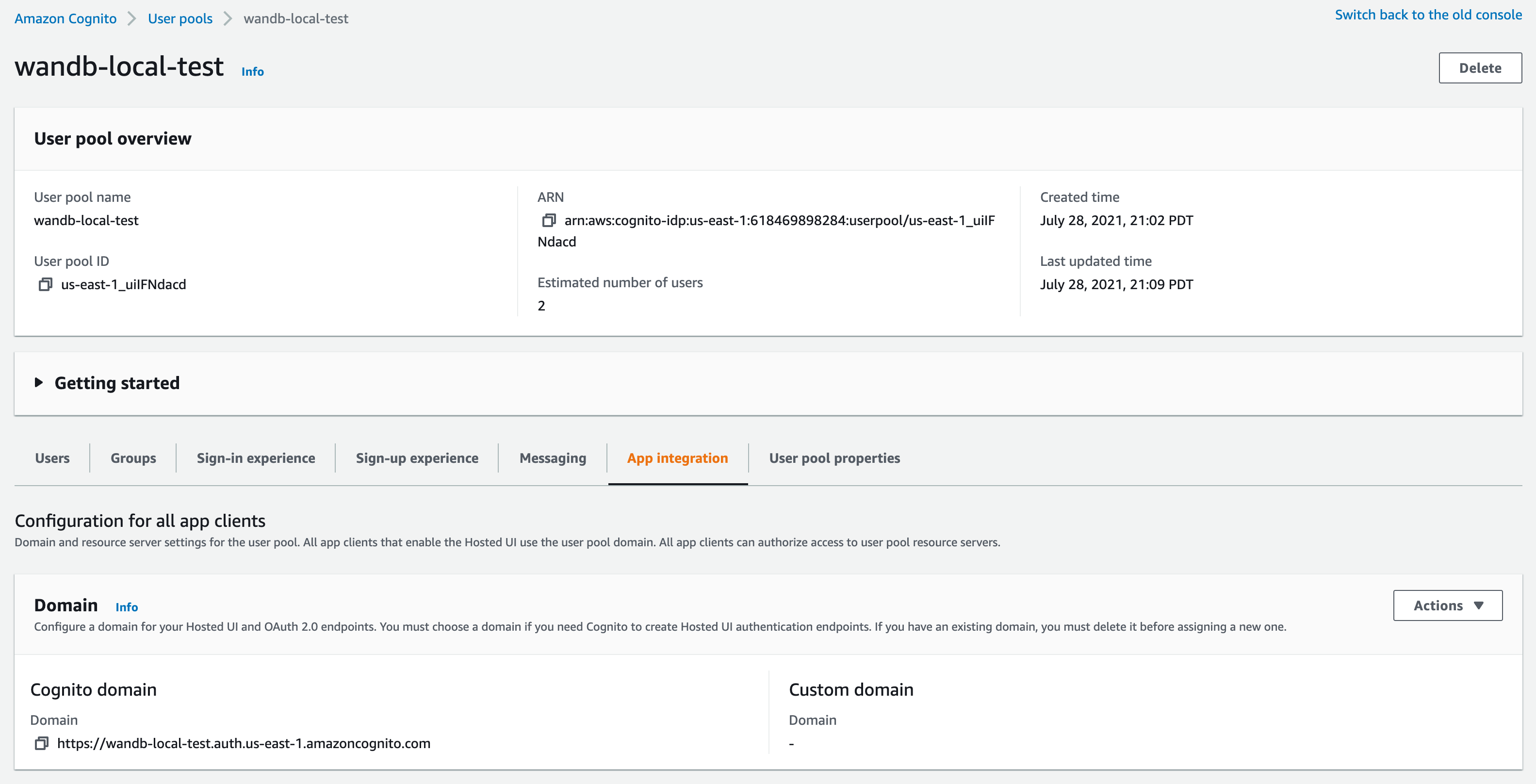
Do not use the "Cognito domain" for the IDP url. Cognito provides it's discovery document at https://cognito-idp.$REGION.amazonaws.com/$USER_POOL_ID
- First set up a new application. Navigate to Okta's App UI and select Add apps:
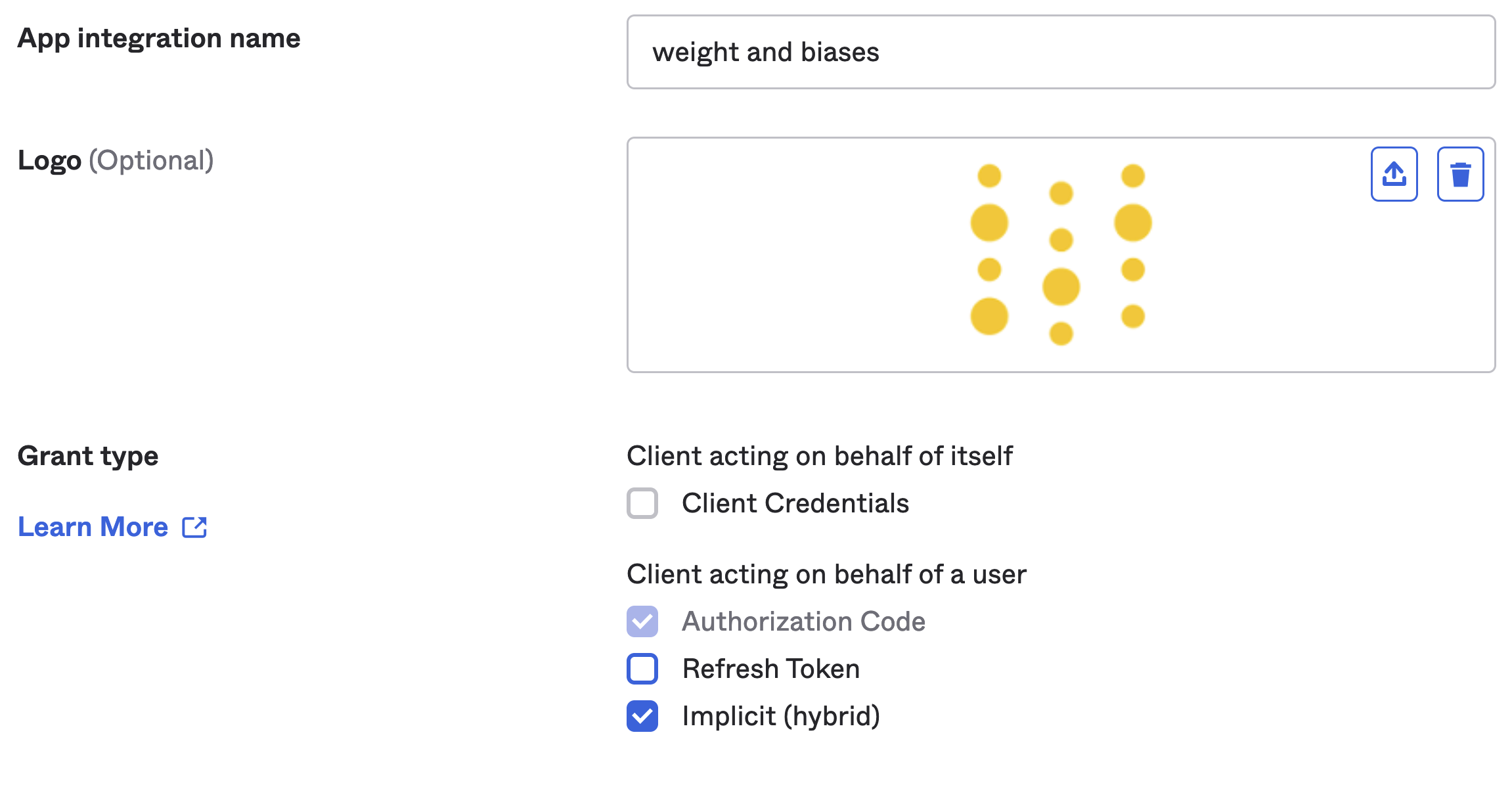
- Provide a name for App in the App Integration name field (for example: Weights and Biases)
- Select grant type
implicit (hybrid)
W&B also supports the Authorization Code grant type with PKCE
Provide an allowed callback url:
- Add the following allowed Callback URL
http(s)://YOUR-W&B-HOST/oidc/callback.
- Add the following allowed Callback URL
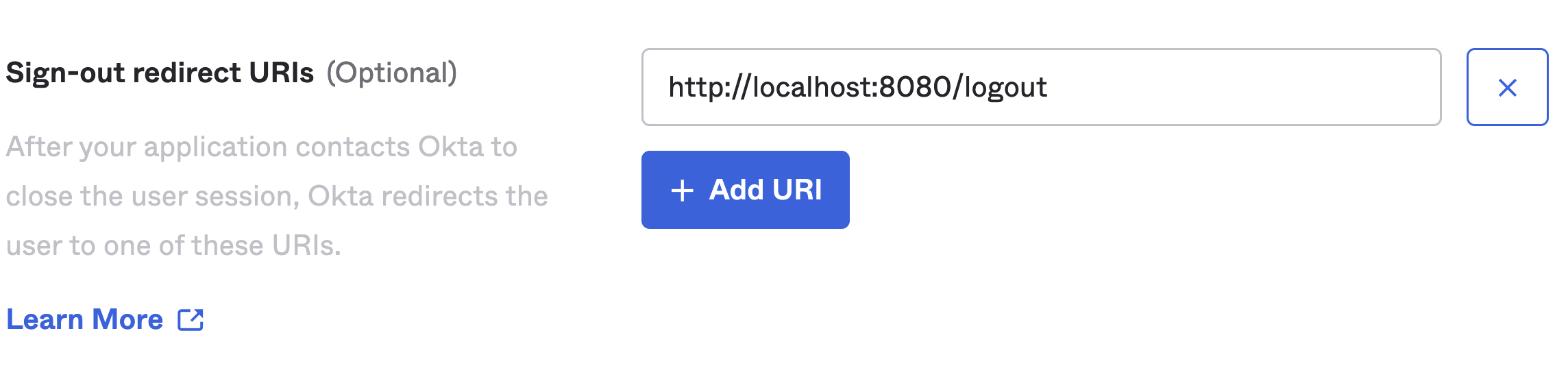
If your IdP supports universal logout, set the Logout URL to
http(s)://YOUR-W&B-HOST.
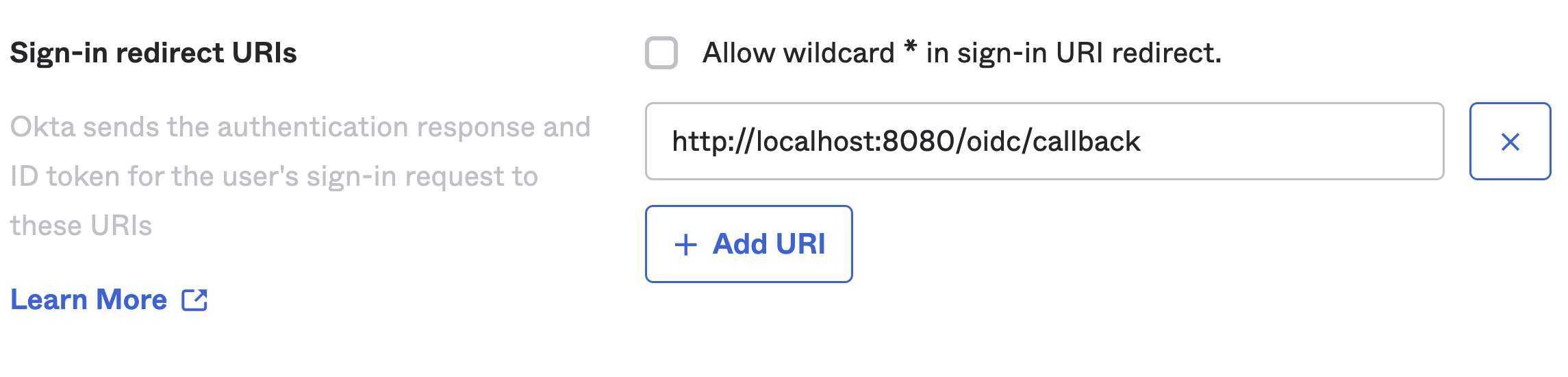 For example, if your application runs in a local host on port 8080 (
For example, if your application runs in a local host on port 8080 (https://localhost:8080),
the redirect URI would look like: https://localhost:8080/oidc/callback.
- Set the sign-out redirect to
http(s)://YOUR-W&B-HOST/logoutin the Sign-out redirects URIs field:
- Provide the OIDC Issuer, Client ID, and Auth method to wandb/local on https://deploy.wandb.ai/system-admin or set them as environment variables.
Configure SSO on the W&B App
Once you have everything configured you can provide the Issuer, Client ID, and Auth method to wandb/local on the W&B App or set environment variables. The following procedure walks you through the steps to configure SSO with the W&B App UI:
- Sign in to your Weights and Biases server
- Navigate to the W&B App.
- From the dropdown, select System Settings:
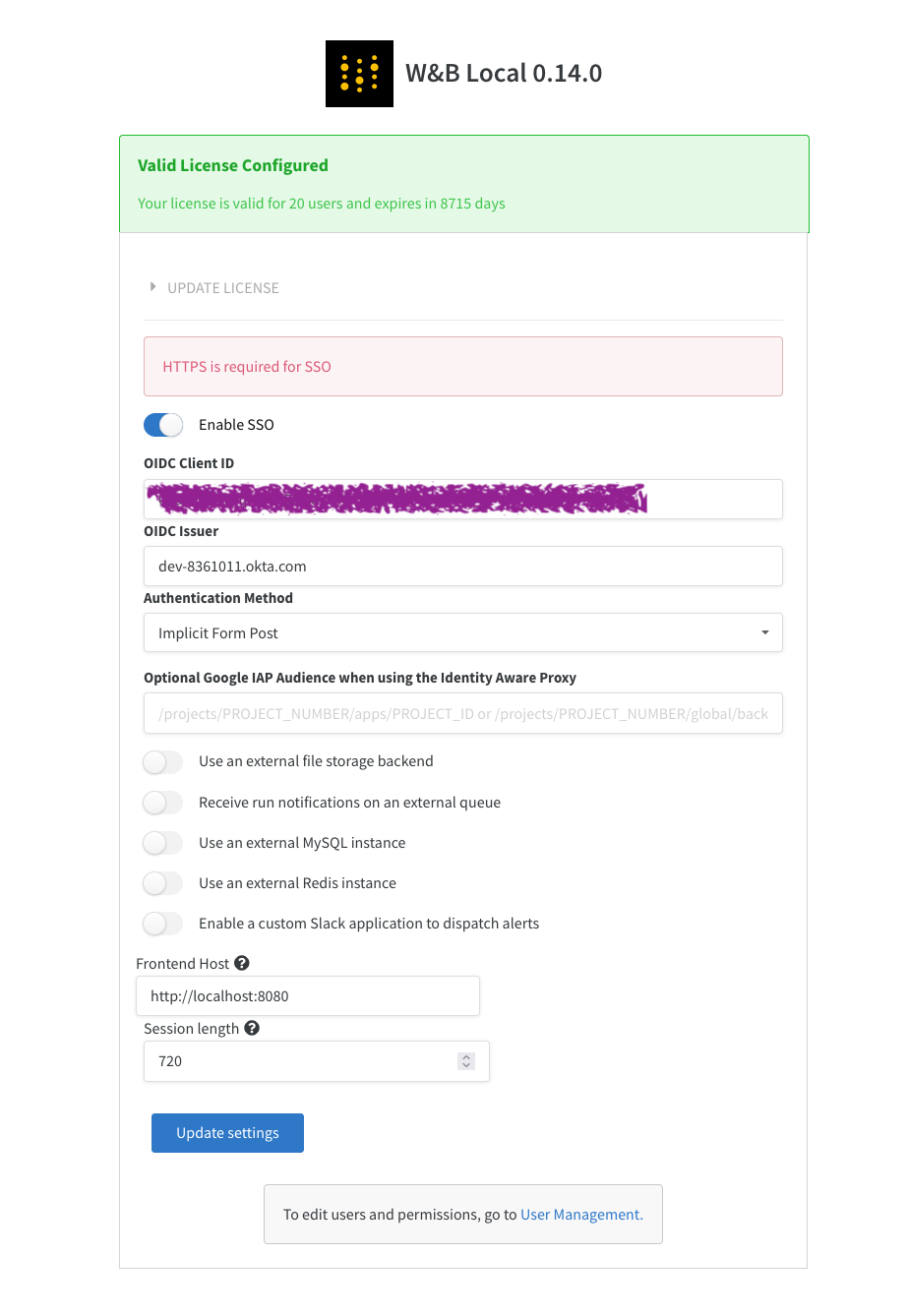
- Enter your Issuer, Client ID, and Authentication Method.
- Select Update settings.
If you're unable to log in to your instance after configuring SSO, you can restart the instance with the LOCAL_RESTORE=true environment variable set. This will output a temporary password to the containers logs and disable SSO. Once you've resolved any issues with SSO, you must remove that environment variable to enable SSO again.